Achieve Military-Grade Security and Instant Compliance
Ensure every layer of your cloud infrastructure is secure, allowing teams to innovate with the peace of mind that their creations are protected.
Security integration empowers organizations to scale with confidence, knowing that their cloud operations are protected by robust compliance controls, a zero-trust security approach, and comprehensive secrets management. With Control Plane, teams can focus on innovation while our platform fortifies their infrastructure, fostering a secure and compliant environment for growth.
Scale with Compliance
Instant Compliance Controls
Control Plane is SOC 2 Type II, PCI DSS Level 1, HIPAA, HITRUST, and GDPR compliant, ensuring your cloud operations meet the highest industry standards from day one.
Most regulated organizations (e.g. banks) whether operating in a multi-cloud environment, or a single cloud, are concerned with the risk of not being compliant. Organizations leveraging the Control Plane Platform instantly gain important compliance controls, operating integrity and standardized audit processes across multiple operating environments.
Enhanced productivity through reduced compliance burden
Engineering teams gain the freedom to focus on functionality and development without being mired in infrastructure or compliance concerns.
Without being burdened with complex compliance requirements, engineering teams gain the freedom to focus on functionality and development without being mired in infrastructure/compliance concerns.
Control Plane's abstraction of security and compliance allows for least-privilege access and the ability to extend policies and standards across different cloud providers.
Engineers have reported an order of magnitude increase in productivity, due to the scope reduction around compliance, observability, auditability and general security controls.
Continuous Security Verification
Control Plane embraces a zero-trust security approach, with continuous identity verification, least-privilege access, continuous monitoring, micro-segmentation, and encryption. This holistic strategy enhances the overall security and integrity of your systems. Control Plane holds SOC 2 Type II compliance and PCI DSS Level 1 compliance.
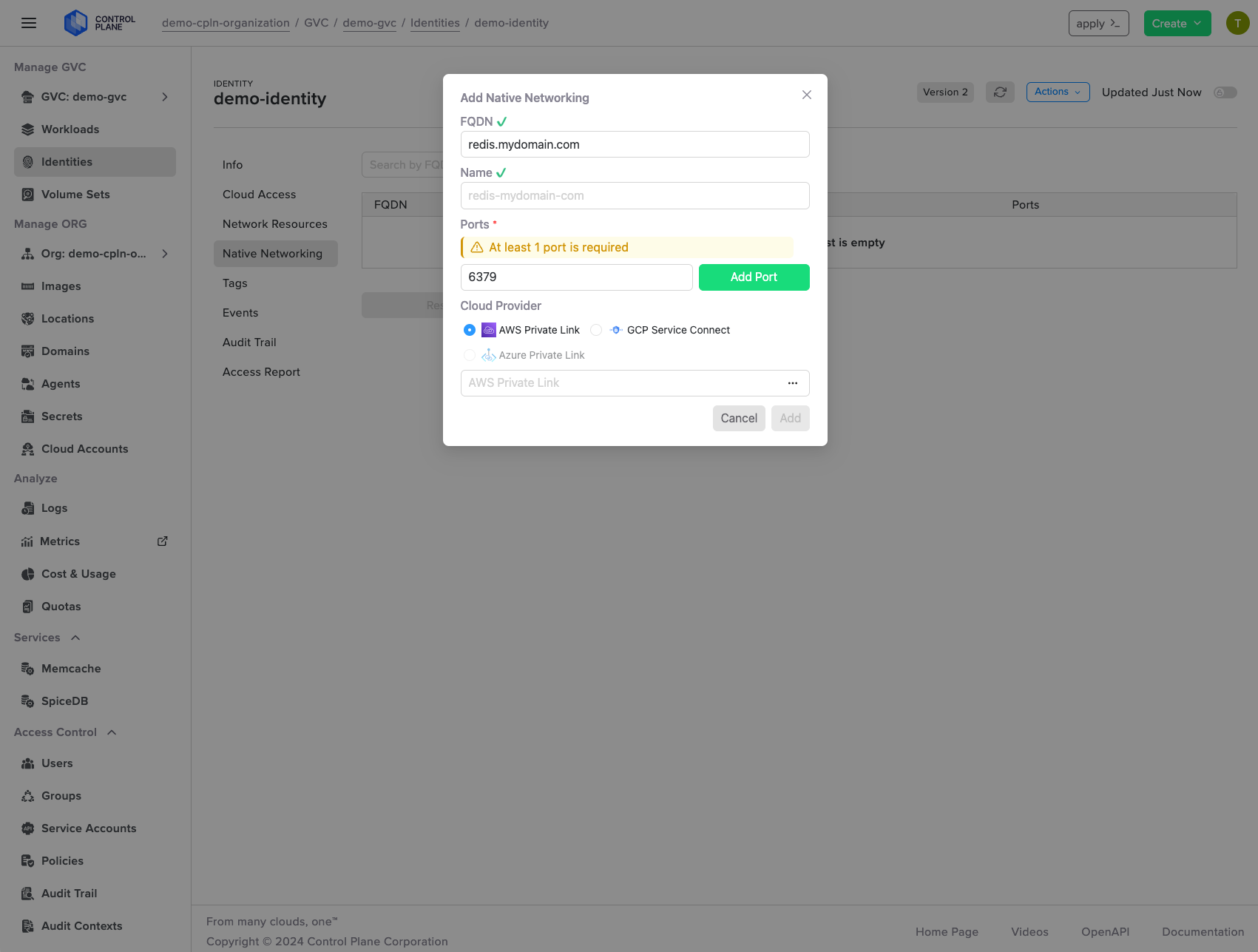
Secure networking across clouds
Cloud Wormhole® provides secure access to private network resources.
Leverage Control Plane's unique technology, a software-defined VPN implementing the Wireguard protocol, to enable secure resource access across clouds. Workloads can securely reach network resources that are otherwise unreachable, such as endpoints inside a VPC not exposed to the internet or in private data center networks.
Additionally, Control Plane supports VPC peering, AWS Private Link, and equivalent private link methods on Azure and GCP, enabling cross-cloud secure networking that spans across one or multiple clouds.
Cloud Wormhole™ revolutionizes secure, software-defined VPN connectivity to your cloud resources. Grant workloads precise access to specific network services while enforcing granular access control. For example, enable a workload deployed within a GVC™ with AWS locations to securely access an RDS in an AWS VPC, inheriting the required permissions encapsulated within the identity.
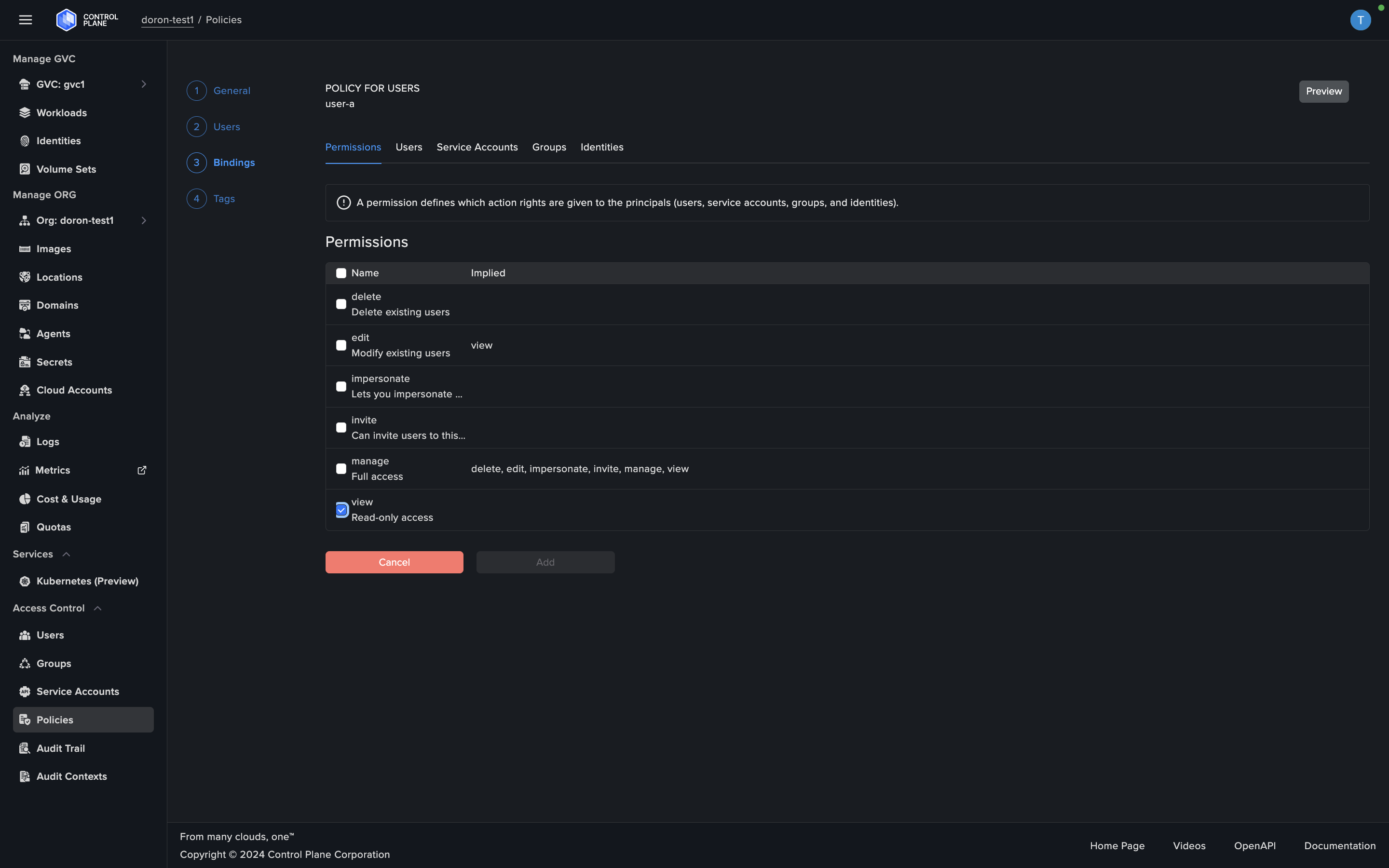
Fine-Grained Access Control
Create detailed access control policies that define who can access what, down to the finest detail. This means you can assign specific responsibilities and control levels to different teams and individuals, ensuring that everyone has just the right amount of access they need.
Resource-Specific Permissions
Our platform allows you to define precise permissions for every resource in your organization. You can map actions like create, delete, and edit to specific users, service accounts, groups, or identities. This ensures that each entity has only the necessary access, enhancing your overall security while maintaining operational efficiency.
Utilize Control Plane's flexible resource types and access policies to granularly manage user and role-based permissions, ensuring a robust zero-trust security posture for your cloud infrastructure.
Immutable Record of Actions
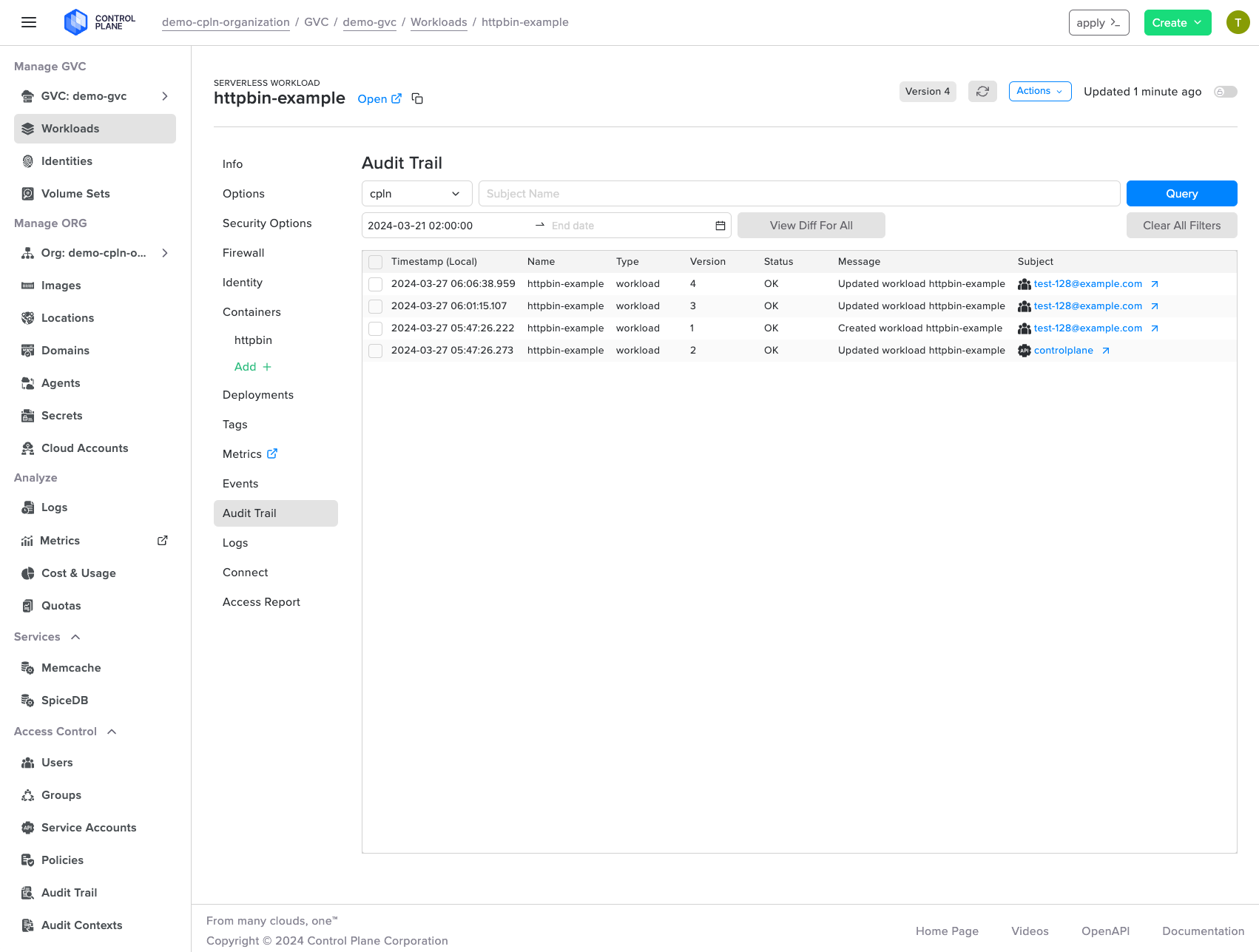
Comprehensive Audit Trail
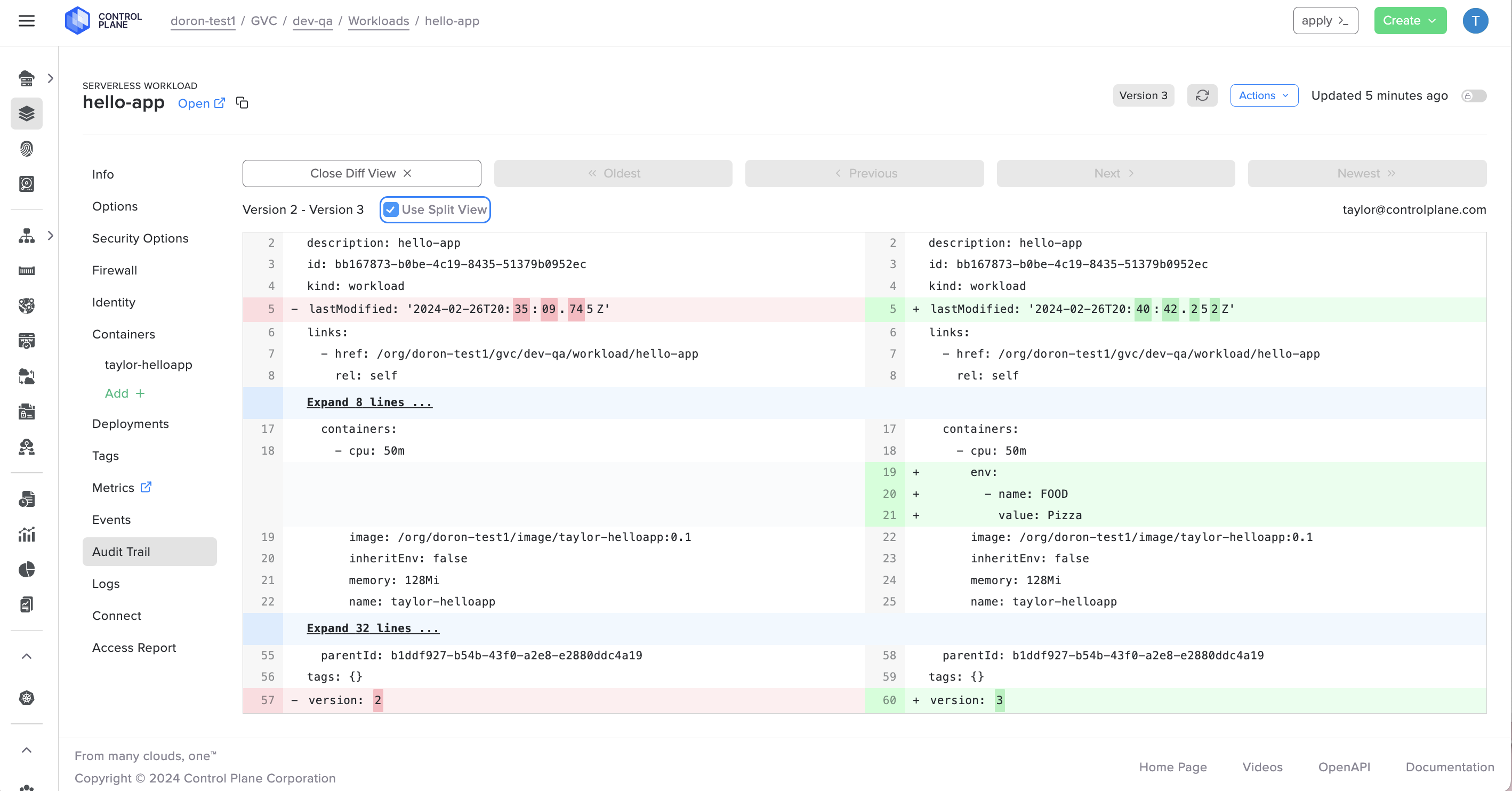
Control Plane's audit trail service provides an immutable record of all resource mutations, whether initiated by the API, CLI, UI, Terraform, or other means. Users can leverage a user-friendly interface to search, filter, and review these actions, gaining visibility into timestamps, resource details, user information, and raw event data.
Streamlined Audit Review
Apply filters to refine the displayed actions based on resource type, audit context, resource name or ID, subject name, and date range, streamlining the audit review process and ensuring compliance with ease.
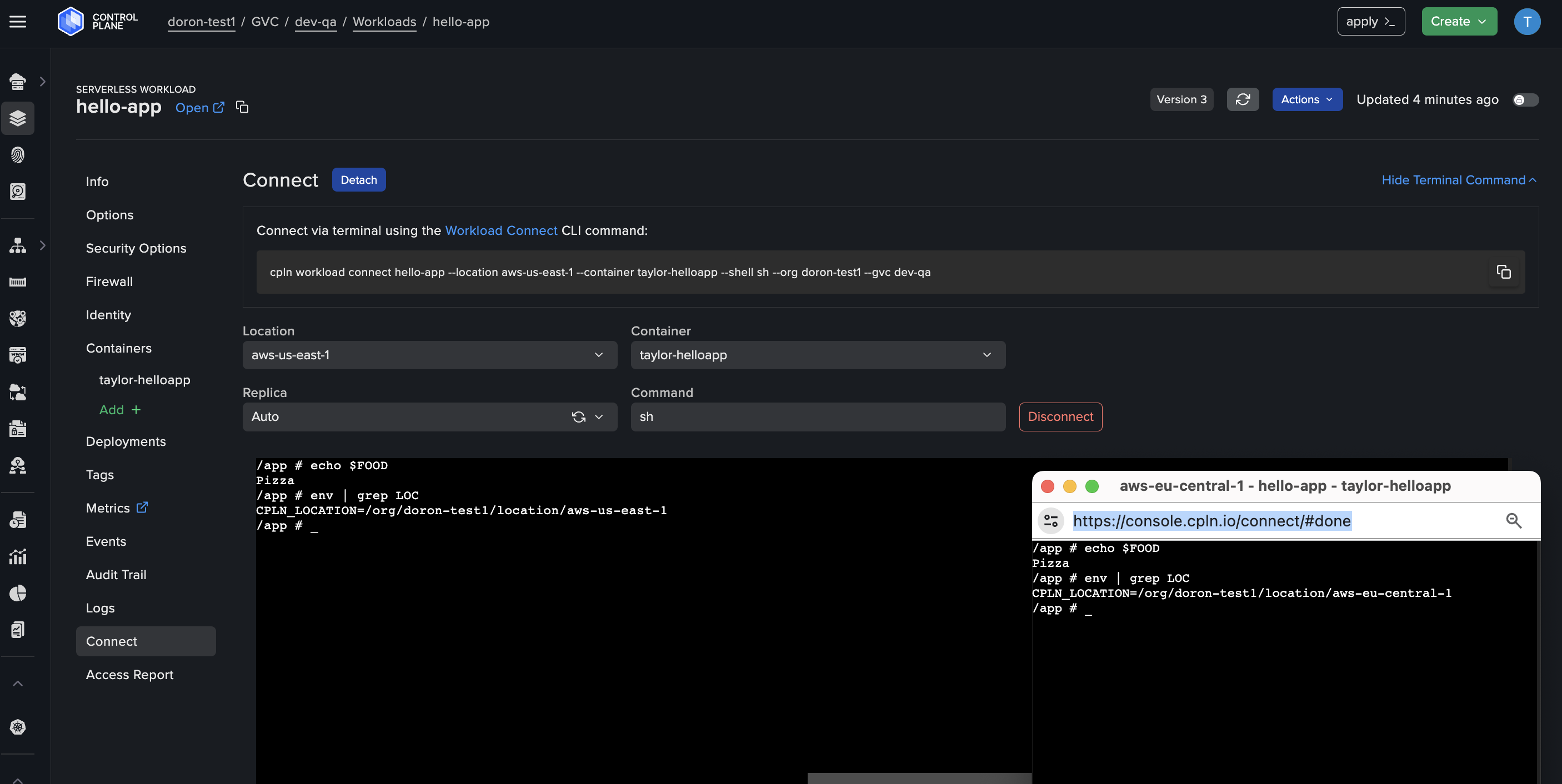
Effortlessly and securely SSH into your application’s container(s) deployed to any location.
The audit trail UI (and API) provides the details of each recorded action, including:
Timestamp
Name of resource
Kind of resource
Version
Results
Message
Subject (the user that acted), their IP address and other attributes, such as authentication type, user ID, email, etc.
Link to display the raw JSON of the events
Control Plane's comprehensive tamper-proof audit trail capabilities offer a complete, immutable record of all actions within your cloud environment. Easily execute custom queries into your infrastructure history for compliance assurance and effortless issue investigation.
You can apply filters to streamline the displayed actions based on:
Resource Type
Audit Context
Resource name or ID
Subject Name
Start and optional end date
A sample of the audit trail UI is provided below, showcasing the outcome of a query that displays all actions that occurred.
Control Plane's comprehensive audit trail empowers you to effortlessly review and analyze all changes made to your cloud resources. Quickly identify and investigate modifications through the intuitive user interface.
Comprehensive Secrets Management
Simplified and standardized secrets management across environments.
Workloads often require sensitive data such as API keys and connection strings. Various challenges, including hardcoded secrets, inadequate encryption practices, access control issues, neglect of regular rotation, insufficient monitoring, potential human errors, dependence on single points of failure, and limited visibility into secrets usage, can compromise the efficacy of secrets management.
Control Plane's comprehensive secrets management subsystem reduces the cognitive load for software and DevOps engineers by providing a secure and standardized approach to managing secrets across any cloud or on-premises environment.
Seamless Secrets Injection
Secrets can be seamlessly injected into containers as environment variables or mounted as files, enhancing security and reducing the risk of exposure. Control Plane greatly simplifies and standardizes secrets management across any cloud or on-prem environment.